Ethical hacking
#hackers #becomehacker #hacking
Welcome To the HackerJoe Channel. Joe is here, I'm all about helping you to know the best and most amazing things about hacking.
Join our growing community
Buy hacker hoodies:- https://ab0f45-2.myshopify.com/
Where else you can find me:
Twitter:- http://twitter.com/hackerjoee
Find the EXACT location of any device on the internet and access its camera and microphone! This video will teach you how how to do all of that using a simple link!
🔴 Get $100 FREE credit on Linode to create your own cloud server (Valid for 60 days)👇
https://www.linode.com/zsecurity
---------------------------------------------------------------
🧠 My Hacking Masterclass👇
https://zsecurity.org/courses/masterc...
🧠 My other hacking courses 👇
https://zsecurity.org/courses/
🌟 VIP Membership (Discord) 👇
https://zsecurity.org/vip-membership/
---------------------------------------------------------------
zSecurity Company - https://zsecurity.com/
Community - https://zsecurity.org/
Facebook - https://www.facebook.com/ZSecurity-14...
Twitter - https://twitter.com/_zSecurity_
Instagram - https://www.instagram.com/zsecurity_org/
Linkedin - https://www.linkedin.com/company/zsecurity-org/
TikTok - https://www.tiktok.com/@zsecurity_org
---------------------------------------------------------------
⚠️ This video is made for educational purposes only, we only test devices and systems that we own or have permission to test, you should not test the security of devices that you do not own or do not have permission to test. ⚠️
---------------------------------------------------------------
Resources:
Track Phone & Computers on The Internet 🌎
https://youtu.be/fZtWRzcmh0Y
CRAZY Fast Password Hacking Using Cloud GPU
https://youtu.be/s4jhe4XsoZI
Storm Breaker Github Repo
https://github.com/ultrasecurity/Storm-Breaker
---------------------------------------------------------------
Time Stamps:
00:00 - intro
00:29 - Thanks to Linode :)
01:26 - Software Installation
05:15 - Tunneling
08:36 - Storm Breaker Usage
11:06 - Tracking Computers
13:00 - Tracking Mobiles
14:03 - Accessing the Camera
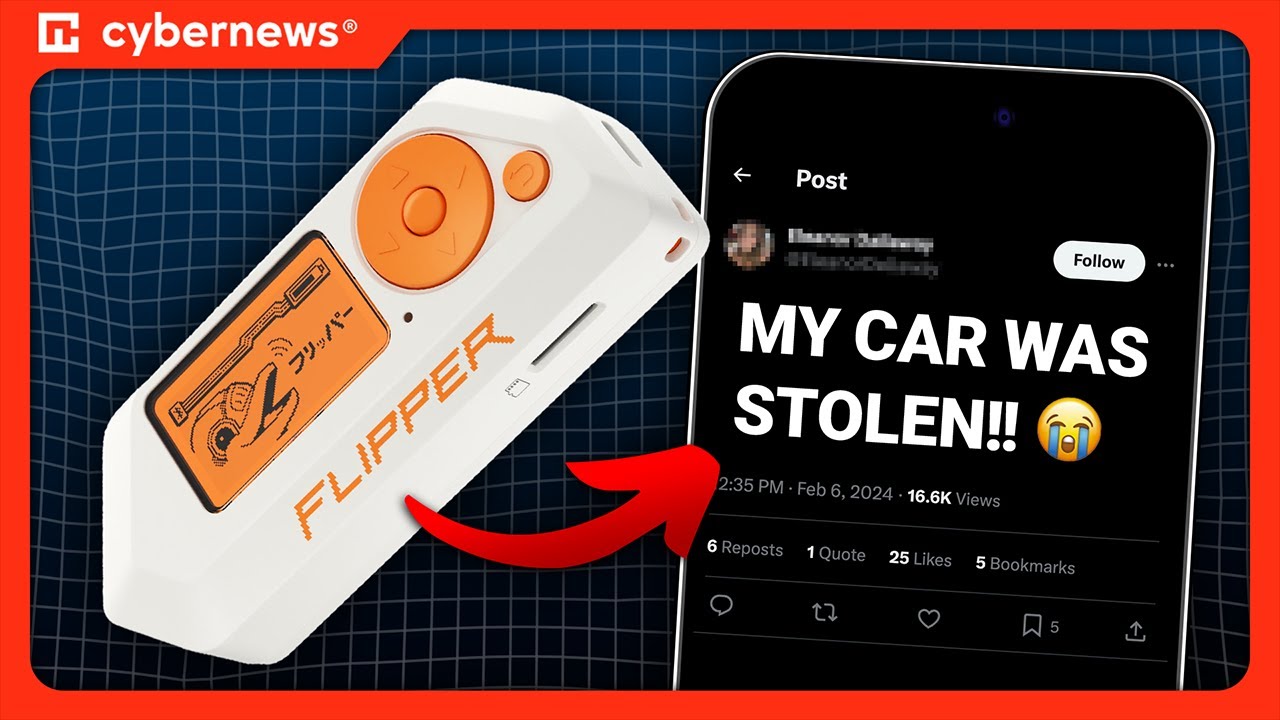
In this video, we will be discussing if its possible to steal a car with the infamous Flipper Zero.
🔑 Protect YOUR accounts - Get THE BEST password manager offer - https://cnews.link/get-nordpass/je30z5MTPAc/
🥷 Secure your online activities - Check out a VPN with the best discount - https://cnews.link/get-nordvpn/je30z5MTPAc/
🦠 Protect yourself from malware - Grab an EXCLUSIVE Antivirus deal - https://cnews.link/get-bitdefender/je30z5MTPAc/
📰 Wondering what's been happening in the world of cybersecurity? Get a quick rundown of the latest news and events in our recap series:
https://youtu.be/-fh-AN4ZcK0
https://youtu.be/KYvys-5lY1M
💌 Stay up-to-date on the latest cybersecurity trends and news by subscribing to our Cybernews newsletter: https://cnews.link/newsletter/
🌐 Looking for even more cybersecurity insights and resources? Visit our website for exclusive content, expert advice, and more: https://cnews.link/website/
💬 Stay connected with us on social media for the latest news, insights, and discussions around cybersecurity: https://linktr.ee/Cybernews
📷 Thinking of purchasing a camera? Check out what is the best camera for you - https://cnews.link/best-cameras/je30z5MTPAc/
ℹ️ About us
We are an independent news outlet with a YouTube channel that posts cybersecurity & tech news videos daily. Our foremost concern is the safety and security of our viewers around the world. We remain vigilant on the issue of hacking and will provide updates as they become available. A number of our investigations and reports have been featured by industry-related publications and global news leaders like Forbes, PC mag, and Techradar.
#cybernews
Occupy The Web (OTW) explains how hacks shown in the Mr Robot TV Series actually work (and if they are actually realistic). He compares real world WiFi, Bluetooth and Scada hacking vs what is shown in the TV series.
In this video we discuss the hacks in Mr Robot Season 1 Episode 6. Which other episodes or technologies do you want us to cover in future videos? Please comment.
Want to learn more from Occupy the Web? You can join his classes using these links:
Hacker's Arise Pro Subscription for $32.99 a month:
https://hackers-arise.com/onli....ne-store/Member-PRO-
Get 3 year's access to all live courses for $750:
https://hackers-arise.com/onli....ne-store/Become-a-Ha
// MENU //
00:00 ▶️ Just By Googling
00:21 ▶️ Welcome Back//OTW
01:13 ▶️ New Series//Hacking with OTW!
01:50 ▶️ Why Mr Robot?
04:47 ▶️ The Hack We're Doing//Mr Robot S1E6
06:27 ▶️ Context//Why Elliot Is Doing This Hack
07:58 ▶️ What is a Rubber Ducky?
09:36 ▶️ Attempt_01//What they try in Mr Robot
11:13 ▶️ Real World//Realistic or Not?
12:44 ▶️ Mr Robot Breakdown//Scanning for Devices
13:25 ▶️ WPA2 Cracked in 30 seconds?
13:41 ▶️ How WPA2 is Cracked
14:13 ▶️ Elliot Discovers a Way In
14:53 ▶️ How to Scan Networks With Your Phone
15:27 ▶️ How to Crack a Network Password
16:10 ▶️ Continued//Elliot Discovers a Way In
16:55 ▶️ Start//Doing the Same Hack
17:17 ▶️ hciconfig
17:52 ▶️ What Bluetooth Adapter Do You Need?
18:26 ▶️ Using Bluetooth Adapter in a VM
19:03 ▶️ Continued//hciconfig
19:43 ▶️ hciconfig in Mr Robot
19:56 ▶️ Next Step//hcitool
21:00 ▶️ Comment!//Should We Do All the Hacks in Mr Robot?
21:53 ▶️ Next Step//hcitool inq
22:03 ▶️ Bluetooth Device Classes
23:18 ▶️ MultiBlue in Mr Robot//What It Does
24:25 ▶️ Next Step//Spooftooph
26:41 ▶️ VMs & Newer Bluetooth Versions//Potential Problems
28:13 ▶️ Summary//Spoofing in Mr Robot
29:20 ▶️ IRL//How This Would Actually Be Done
29:29 ▶️ PLC Block Diagram
29:36 ▶️ Siemens PLC Used for Prison Systems
30:00 ▶️ Typical Prison Design
30:36 ▶️ Prison Door System Schematic
31:16 ▶️ Explained//Ladder Logic
32:46 ▶️ Mr Robot//What is Unrealistic
34:10 ▶️ Finding SCADA Systems//Too Awesome for YouTube
36:34 ▶️ How Vulnerable Are SCADA Systems?
38:54 ▶️ Where to Learn How to Hack SCADA Systems
40:40 ▶️ Learn for Free at Hackers-Arise or Sign Up For Courses
41:23 ▶️ Comment!//What Videos Would You Like to See?
42:50 ▶️ Future Videos with OTW on Mr Robot!
44:32 ▶️ Software Defined Radio for Hackers?
45:00 ▶️ Thank You, OTW!
// Devices used in video //
Hak5 Rubber Ducky: https://davidbombal.wiki/gethak5
Panda Bluetooth 4.0 USB Nano Adapter : https://amzn.to/3NlSlbQ
MultiBlue Dongle USB Bluetooth V3.0 HiD: Not available unfortunately.
// Previous videos //
OTW Hacking Russia: https://youtu.be/GudY7XYouRk
OTW Hacking Scada: https://youtu.be/uXbGQiXsRes
OTW Hacking CCTV: https://youtu.be/ZGCScbV7vSA
// David's SOCIAL //
Discord: https://discord.com/invite/usKSyzb
Twitter: https://www.twitter.com/davidbombal
Instagram: https://www.instagram.com/davidbombal
LinkedIn: https://www.linkedin.com/in/davidbombal
Facebook: https://www.facebook.com/davidbombal.co
TikTok: http://tiktok.com/@davidbombal
YouTube: https://www.youtube.com/davidbombal
// Occupy The Web social //
Twitter: https://twitter.com/three_cube
// Occupy The Web books //
Linux Basics for Hackers: https://amzn.to/3JlAQXe
Getting Started Becoming a Master Hacker: https://amzn.to/3qCQbvh
// Other books //
The Linux Command Line: https://amzn.to/3ihGP3j
How Linux Works: https://amzn.to/3qeCHoY
// Occupy The Web Website / Hackers Arise Website //
Website: https://www.hackers-arise.com/?afmc=1d
How Elliot hacked the prison: https://www.hackers-arise.com/....post/2016/08/14/Mr-R
OTW Mr Robot series: https://www.hackers-arise.com/mr-robot
SCADA Hacking: The Key Differences between Security of SCADA and Traditional IT systems
https://davidbombal.wiki/scada1
Lots of Scada content:
https://www.hackers-arise.com/scada-hacking
// MY STUFF //
https://www.amazon.com/shop/davidbombal
// SPONSORS //
Interested in sponsoring my videos? Reach out to my team here: sponsors@davidbombal.com
hacking
hack
mr robot
mr robot bluetooth
mr robot scada
scada
scada hacking
bluetooth
bluetooth hacking
bluetooth hack
mr robot bluetooth
mr robot season 1 episode 6
mr robot season 1
google dorks
shodan
scada hacks
scada hacking
scada google dorks
wifi
wifi hacking
wpa hacking
wpa2 hacking
wifi hack
wpa2 hack
mr robot wpa
mr robot wpa2
hack scada
bluetooth keyboard hacks
bluetooth panda
panda bluetooth
Disclaimer: This video is for educational purposes only.
Please note that links listed may be affiliate links and provide me with a small percentage/kickback should you use them to purchase any of the items listed or recommended. Thank you for supporting me and this channel!
#wifi #bluetooth #hacking
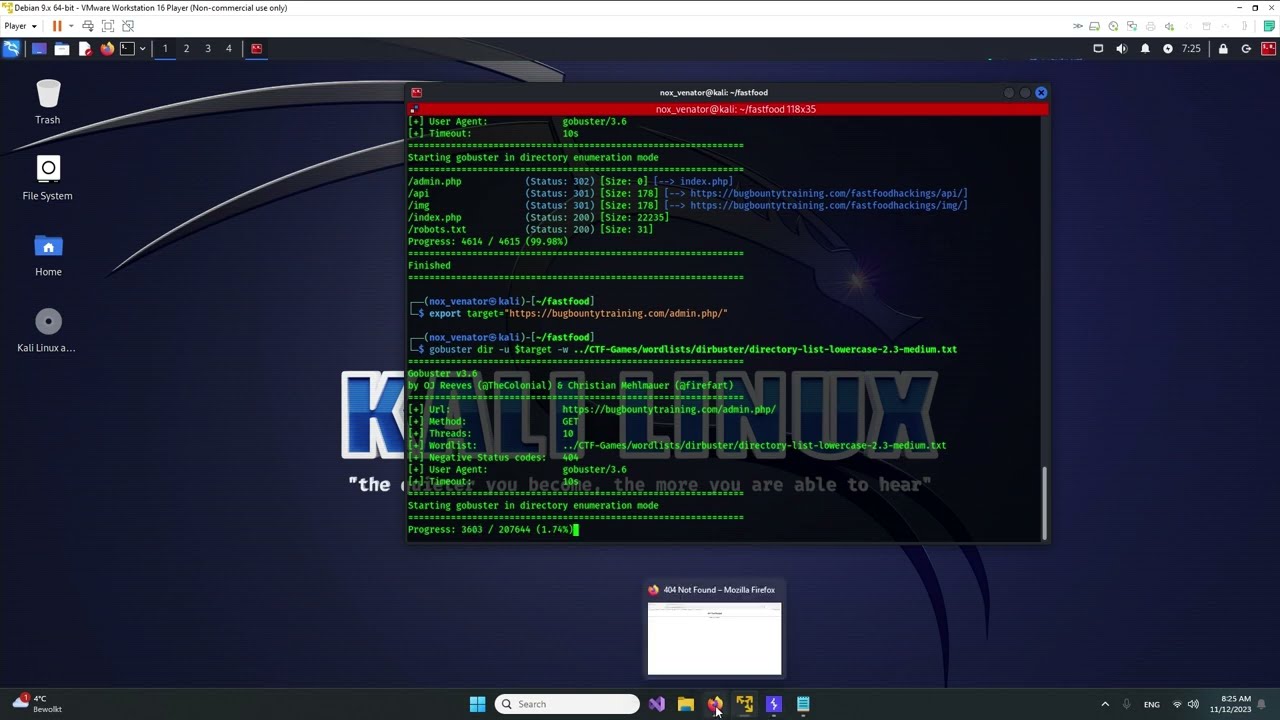
Learn how to hack like a bug bounty hunter in this live hacking tutorial! In this video, I will show you how to find and exploit vulnerabilities in real time, using the same techniques that bug bounty hunters use to earn thousands of dollars every year.
This tutorial is perfect for beginners, but even experienced hackers will learn something new. I will cover everything from the basics of web application security to more advanced techniques like SQL injection and XSS.
By the end of this video, you will be able to think like a bug bounty hunter and start finding vulnerabilities on your own.
This video will show you how hackers can hack CCTV cameras using the IP only!
🔴 Get $100 FREE credit on Linode to create your own cloud server (Valid for 60 days)👇
https://www.linode.com/zsecurity
------------------------------------------------------------------------------------
Maythom personal Youtube channel: https://www.youtube.com/@maythom
zSecurity Company - https://zsecurity.com/
Community - https://zsecurity.org/
Facebook - https://www.facebook.com/ZSecurity-14...
Twitter - https://twitter.com/_zSecurity_
Instagram - https://www.instagram.com/zsecurity_org/
Linkedin - https://www.linkedin.com/company/zsecurity-org/
TikTok - https://www.tiktok.com/@zsecurity_org
-------------------------------------------------------------------------------------
Resources:
Nmap: https://nmap.org/
Shodan search engine : https://www.shodan.io/
Port 554 RTSP: https://www.speedguide.net/port.php?port=554
------------------------------------------------------------------------------------
Timestamps:
0:00 Intro
01:07 Thanks to Linode!
02:00 Scanning the network
05:20 Finding open ports
06:55 Accessing the cctv via browser
10:08 Accessing the cctv via RTSP
14:11 Thank you!
-------------------------------------------------------------------------------------
⚠️ Please be advised that this video is made for educational security purposes only. Also note that you shouldn't test on devices that you don't have permissions to test. We always have the permissions granted to test the accounts/devices used on this channel.
I hereby affirm that the devices employed in this video are under my exclusive ownership, and the primary purpose of this content is strictly educational. It is of great importance to emphasize that this video does not, in any way, endorse or encourage any unethical activities.⚠️
// Membership //
Want to learn all about cyber-security and become an ethical hacker? Join this channel now to gain access into exclusive ethical hacking videos by clicking this link: https://www.youtube.com/channe....l/UC1szFCBUWXY3ESff8
// Courses //
Full Ethical Hacking Course: https://www.udemy.com/course/f....ull-web-ethical-hack
Full Web Ethical Hacking Course: https://www.udemy.com/course/f....ull-web-ethical-hack
Full Mobile Hacking Course: https://www.udemy.com/course/f....ull-mobile-hacking-c
// Books //
Kali Linux Hacking: https://amzn.to/3IUXaJv
Linux Basics for Hackers: https://amzn.to/3EzRPV6
The Ultimate Kali Linux Book: https://amzn.to/3m7cutD
// Social Links //
Website: https://www.loiliangyang.com
Facebook: https://www.facebook.com/Loiliangyang/
Instagram: https://www.instagram.com/loiliangyang/
LinkedIn: https://www.linkedin.com/in/loiliangyang/
// Disclaimer //
Hacking without permission is illegal. This channel is strictly educational for learning about cyber-security in the areas of ethical hacking and penetration testing so that we can protect ourselves against the real hackers.
Digital Sherlock: A Guide to Find Info on People with Open Source Intelligence.
-
// CHAPTERS:
0:00 What is OSINT
0:30 OSINT Example
1:15 Google Dorking
1:47 Finding Documents
2:45 Facial Recognition
2:58 Reverse Image Search
3:26 Find Info on Email
3:51 Searching Social Media Accounts
4:22 Phone Number OSINT
4:35 Intel Techniques
-
// Google Dorks Cheat Sheet
shorturl.at/bdgoE
-
// OSINT Framework
osintframework.com
// Intel Techniques
inteltechniques.com
-
// Follow Me:
Instagram: instagram.com/an0n.ali
Odysee: odysee.com/@an0n.ali:8
WATCH - So, Its Been Their Plan All Along! You Won't Believe It..
Weather modification is the act of intentionally manipulating or altering the weather. The most common form of weather modification is cloud seeding, which increases rain or snow, usually for the purpose of increasing the local water supply. Weather modification can also have the goal of preventing damaging weather, such as hail or hurricanes, from occurring; or of provoking damaging weather against the enemy, as a tactic of military or economic warfare like Operation Popeye, where clouds were seeded to prolong the monsoon in Vietnam. Weather modification in warfare has been banned by the United Nations under the Environmental Modification Convention.
Speaker:
Jon Bowne
FOLLOW FOR MORE:
YouTube @-anonymous
Twitter https://twitter.com/anonymousofcl
Subscribe and Activate the 🔔 beside the subscribe button to get a notification! Leave a comment what you think.
Please SHARE this as widely as you feel drawn...
Content licensed
Related:
weather modification
weather modification
weather modification
Keywords:
end times productions message strange truth world news current events september 2023 today this week this month motivation america weather
@EndTimesProductions
Available to rent and own from 14th August.
Dynamic and eye-opening, BILLION DOLLAR HEIST tells the story of the most daring cyber heist of all time, the Bangladeshi Central Bank theft. This feature documentary traces the origins of cyber-crime from basic credit card fraud to the wildly complex criminal organisations in existence today. A tale of epic proportions, Billion Dollar Heist shows how the key players on both sides of the law are embroiled in a global game of cat-and-mouse – with our money and security on the line.
Yours to Own Digital 8/15: https://www.uphe.com/movies/billion-dollar-heist
Sign-up to receive updates, sneak peeks and offers here: http://uni.pictures/emailyt
The Universal Pictures All-Access channel is the place to be for all things about movies and behind-the-scenes. Subscribe to our channel to keep up on all the latest videos. Also, access hundreds of movies instantly. No planning, no waiting, no schedules. Buy or Rent hundreds of movies right now - right here on Youtube!
Subscribe to Our Channel: http://uni.pictures/ytumsubscribe
#movieclips
// Membership //
Want to learn all about cyber-security and become an ethical hacker? Join this channel now to gain access into exclusive ethical hacking videos by clicking this link: https://www.youtube.com/channe....l/UC1szFCBUWXY3ESff8
// Courses //
Full Ethical Hacking Course: https://www.udemy.com/course/f....ull-web-ethical-hack
Full Web Ethical Hacking Course: https://www.udemy.com/course/f....ull-web-ethical-hack
Full Mobile Hacking Course: https://www.udemy.com/course/f....ull-mobile-hacking-c
// Books //
Kali Linux Hacking: https://amzn.to/3IUXaJv
Linux Basics for Hackers: https://amzn.to/3EzRPV6
The Ultimate Kali Linux Book: https://amzn.to/3m7cutD
// Social Links //
Website: https://www.loiliangyang.com
Facebook: https://www.facebook.com/Loiliangyang/
Instagram: https://www.instagram.com/loiliangyang/
LinkedIn: https://www.linkedin.com/in/loiliangyang/
// Disclaimer //
Hacking without permission is illegal. This channel is strictly educational for learning about cyber-security in the areas of ethical hacking and penetration testing so that we can protect ourselves against the real hackers.
// Membership //
Want to learn all about cyber-security and become an ethical hacker? Join this channel now to gain access into exclusive ethical hacking videos by clicking this link: https://www.youtube.com/channe....l/UC1szFCBUWXY3ESff8
// Courses //
Full Ethical Hacking Course: https://www.udemy.com/course/f....ull-web-ethical-hack
Full Web Ethical Hacking Course: https://www.udemy.com/course/f....ull-web-ethical-hack
Full Mobile Hacking Course: https://www.udemy.com/course/f....ull-mobile-hacking-c
// Books //
Kali Linux Hacking: https://amzn.to/3IUXaJv
Linux Basics for Hackers: https://amzn.to/3EzRPV6
The Ultimate Kali Linux Book: https://amzn.to/3m7cutD
// Social Links //
Website: https://www.loiliangyang.com
Facebook: https://www.facebook.com/Loiliangyang/
Instagram: https://www.instagram.com/loiliangyang/
LinkedIn: https://www.linkedin.com/in/loiliangyang/
// Disclaimer //
Hacking without permission is illegal. This channel is strictly educational for learning about cyber-security in the areas of ethical hacking and penetration testing so that we can protect ourselves against the real hackers.
// Membership //
Want to learn all about cyber-security and become an ethical hacker? Join this channel now to gain access into exclusive ethical hacking videos by clicking this link: https://www.youtube.com/channe....l/UC1szFCBUWXY3ESff8
// Courses //
Full Ethical Hacking Course: https://www.udemy.com/course/f....ull-web-ethical-hack
Full Web Ethical Hacking Course: https://www.udemy.com/course/f....ull-web-ethical-hack
Full Mobile Hacking Course: https://www.udemy.com/course/f....ull-mobile-hacking-c
// Books //
Kali Linux Hacking: https://amzn.to/3IUXaJv
Linux Basics for Hackers: https://amzn.to/3EzRPV6
The Ultimate Kali Linux Book: https://amzn.to/3m7cutD
// Social Links //
Website: https://www.loiliangyang.com
Facebook: https://www.facebook.com/Loiliangyang/
Instagram: https://www.instagram.com/loiliangyang/
LinkedIn: https://www.linkedin.com/in/loiliangyang/
// Disclaimer //
Hacking without permission is illegal. This channel is strictly educational for learning about cyber-security in the areas of ethical hacking and penetration testing so that we can protect ourselves against the real hackers.
// Membership //
Want to learn all about cyber-security and become an ethical hacker? Join this channel now to gain access into exclusive ethical hacking videos by clicking this link: https://www.youtube.com/channe....l/UC1szFCBUWXY3ESff8
// Courses //
Full Ethical Hacking Course: https://www.udemy.com/course/f....ull-web-ethical-hack
Full Web Ethical Hacking Course: https://www.udemy.com/course/f....ull-web-ethical-hack
Full Mobile Hacking Course: https://www.udemy.com/course/f....ull-mobile-hacking-c
// Books //
Kali Linux Hacking: https://amzn.to/3IUXaJv
Linux Basics for Hackers: https://amzn.to/3EzRPV6
The Ultimate Kali Linux Book: https://amzn.to/3m7cutD
// Social Links //
Website: https://www.loiliangyang.com
Facebook: https://www.facebook.com/Loiliangyang/
Instagram: https://www.instagram.com/loiliangyang/
LinkedIn: https://www.linkedin.com/in/loiliangyang/
// Disclaimer //
Hacking without permission is illegal. This channel is strictly educational for learning about cyber-security in the areas of ethical hacking and penetration testing so that we can protect ourselves against the real hackers.
// Membership //
Want to learn all about cyber-security and become an ethical hacker? Join this channel now to gain access into exclusive ethical hacking videos by clicking this link: https://www.youtube.com/channe....l/UC1szFCBUWXY3ESff8
// Courses //
Full Ethical Hacking Course: https://www.udemy.com/course/f....ull-web-ethical-hack
Full Web Ethical Hacking Course: https://www.udemy.com/course/f....ull-web-ethical-hack
Full Mobile Hacking Course: https://www.udemy.com/course/f....ull-mobile-hacking-c
// Books //
Kali Linux Hacking: https://amzn.to/3IUXaJv
Linux Basics for Hackers: https://amzn.to/3EzRPV6
The Ultimate Kali Linux Book: https://amzn.to/3m7cutD
// Social Links //
Website: https://www.loiliangyang.com
Facebook: https://www.facebook.com/Loiliangyang/
Instagram: https://www.instagram.com/loiliangyang/
LinkedIn: https://www.linkedin.com/in/loiliangyang/
// Disclaimer //
Hacking without permission is illegal. This channel is strictly educational for learning about cyber-security in the areas of ethical hacking and penetration testing so that we can protect ourselves against the real hackers.
// Membership //
Want to learn all about cyber-security and become an ethical hacker? Join this channel now to gain access into exclusive ethical hacking videos by clicking this link: https://www.youtube.com/channe....l/UC1szFCBUWXY3ESff8
// Courses //
Full Ethical Hacking Course: https://www.udemy.com/course/f....ull-web-ethical-hack
Full Web Ethical Hacking Course: https://www.udemy.com/course/f....ull-web-ethical-hack
Full Mobile Hacking Course: https://www.udemy.com/course/f....ull-mobile-hacking-c
// Books //
Kali Linux Hacking: https://amzn.to/3IUXaJv
Linux Basics for Hackers: https://amzn.to/3EzRPV6
The Ultimate Kali Linux Book: https://amzn.to/3m7cutD
// Social Links //
Website: https://www.loiliangyang.com
Facebook: https://www.facebook.com/Loiliangyang/
Instagram: https://www.instagram.com/loiliangyang/
LinkedIn: https://www.linkedin.com/in/loiliangyang/
// Disclaimer //
Hacking without permission is illegal. This channel is strictly educational for learning about cyber-security in the areas of ethical hacking and penetration testing so that we can protect ourselves against the real hackers.
// Membership //
Want to learn all about cyber-security and become an ethical hacker? Join this channel now to gain access into exclusive ethical hacking videos by clicking this link: https://www.youtube.com/channe....l/UC1szFCBUWXY3ESff8
// Courses //
Full Ethical Hacking Course: https://www.udemy.com/course/f....ull-web-ethical-hack
Full Web Ethical Hacking Course: https://www.udemy.com/course/f....ull-web-ethical-hack
Full Mobile Hacking Course: https://www.udemy.com/course/f....ull-mobile-hacking-c
// Books //
Kali Linux Hacking: https://amzn.to/3IUXaJv
Linux Basics for Hackers: https://amzn.to/3EzRPV6
The Ultimate Kali Linux Book: https://amzn.to/3m7cutD
// Social Links //
Website: https://www.loiliangyang.com
Facebook: https://www.facebook.com/Loiliangyang/
Instagram: https://www.instagram.com/loiliangyang/
LinkedIn: https://www.linkedin.com/in/loiliangyang/
// Disclaimer //
Hacking without permission is illegal. This channel is strictly educational for learning about cyber-security in the areas of ethical hacking and penetration testing so that we can protect ourselves against the real hackers.
// Membership //
Want to learn all about cyber-security and become an ethical hacker? Join this channel now to gain access into exclusive ethical hacking videos by clicking this link: https://www.youtube.com/channe....l/UC1szFCBUWXY3ESff8
// Courses //
Full Ethical Hacking Course: https://www.udemy.com/course/f....ull-web-ethical-hack
Full Web Ethical Hacking Course: https://www.udemy.com/course/f....ull-web-ethical-hack
Full Mobile Hacking Course: https://www.udemy.com/course/f....ull-mobile-hacking-c
// Books //
Kali Linux Hacking: https://amzn.to/3IUXaJv
Linux Basics for Hackers: https://amzn.to/3EzRPV6
The Ultimate Kali Linux Book: https://amzn.to/3m7cutD
// Social Links //
Website: https://www.loiliangyang.com
Facebook: https://www.facebook.com/Loiliangyang/
Instagram: https://www.instagram.com/loiliangyang/
LinkedIn: https://www.linkedin.com/in/loiliangyang/
// Disclaimer //
Hacking without permission is illegal. This channel is strictly educational for learning about cyber-security in the areas of ethical hacking and penetration testing so that we can protect ourselves against the real hackers.
// Membership //
Want to learn all about cyber-security and become an ethical hacker? Join this channel now to gain access into exclusive ethical hacking videos by clicking this link: https://www.youtube.com/channe....l/UC1szFCBUWXY3ESff8
// Courses //
Full Ethical Hacking Course: https://www.udemy.com/course/f....ull-web-ethical-hack
Full Web Ethical Hacking Course: https://www.udemy.com/course/f....ull-web-ethical-hack
Full Mobile Hacking Course: https://www.udemy.com/course/f....ull-mobile-hacking-c
// Books //
Kali Linux Hacking: https://amzn.to/3IUXaJv
Linux Basics for Hackers: https://amzn.to/3EzRPV6
The Ultimate Kali Linux Book: https://amzn.to/3m7cutD
// Social Links //
Website: https://www.loiliangyang.com
Facebook: https://www.facebook.com/Loiliangyang/
Instagram: https://www.instagram.com/loiliangyang/
LinkedIn: https://www.linkedin.com/in/loiliangyang/
// Disclaimer //
Hacking without permission is illegal. This channel is strictly educational for learning about cyber-security in the areas of ethical hacking and penetration testing so that we can protect ourselves against the real hackers.
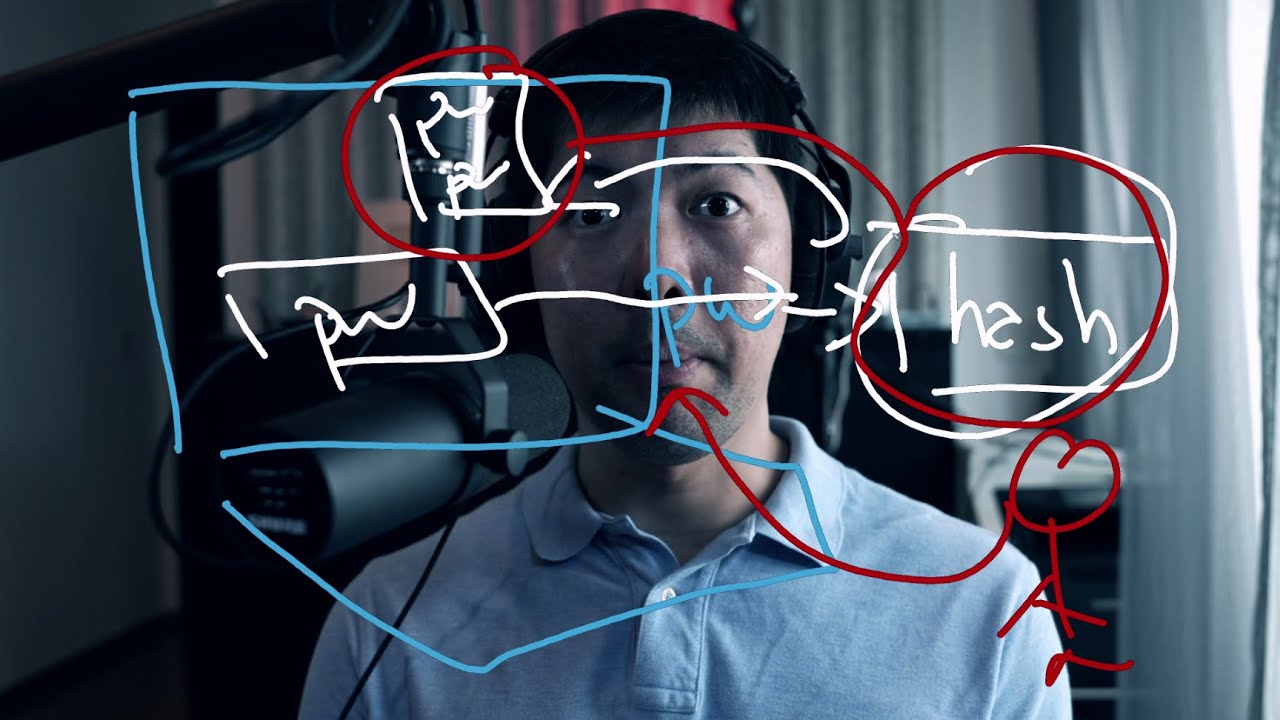
Pass the Hash technique
// Membership //
Want to learn all about cyber-security and become an ethical hacker? Join this channel now to gain access into exclusive ethical hacking videos by clicking this link: https://www.youtube.com/channe....l/UC1szFCBUWXY3ESff8
// Courses //
Full Ethical Hacking Course: https://www.udemy.com/course/f....ull-web-ethical-hack
Full Web Ethical Hacking Course: https://www.udemy.com/course/f....ull-web-ethical-hack
Full Mobile Hacking Course: https://www.udemy.com/course/f....ull-mobile-hacking-c
// Books //
Kali Linux Hacking: https://amzn.to/3IUXaJv
Linux Basics for Hackers: https://amzn.to/3EzRPV6
The Ultimate Kali Linux Book: https://amzn.to/3m7cutD
// Social Links //
Website: https://www.loiliangyang.com
Facebook: https://www.facebook.com/Loiliangyang/
Instagram: https://www.instagram.com/loiliangyang/
LinkedIn: https://www.linkedin.com/in/loiliangyang/
// Disclaimer //
Hacking without permission is illegal. This channel is strictly educational for learning about cyber-security in the areas of ethical hacking and penetration testing so that we can protect ourselves against the real hackers.